global marketing, integrated marketing project manager
- FMA
- The Fabricator
- FABTECH
- Canadian Metalworking
5 tips for protecting industrial networks
OT/IT convergence introduces new attacks in industrial control systems
- By Alvis Chen
- January 24, 2022
- Article
- Management
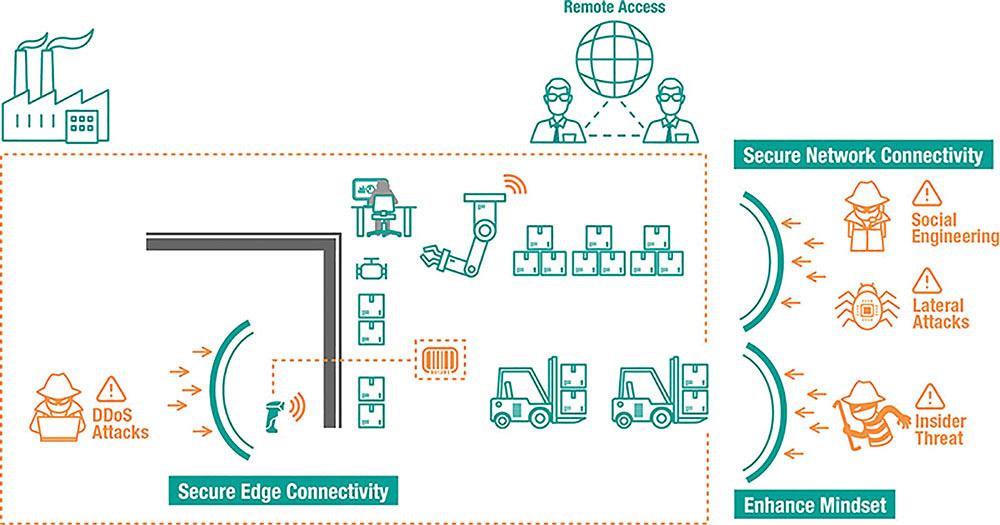
Commitment from management forms the foundation of a cybersecurity protocol. The first step is a risk assessment, which is followed by security programs and policies being implemented. Moxa
As the operational technology (OT) and information technology (IT) convergence trend continues to gather momentum, several attacks are made possible in industrial control systems. Although some of these are existing vulnerabilities, some are unknown. Therefore, everyone from the C-suite to the plant floor needs to join forces to enhance industrial cybersecurity.
It has been noted that cybersecurity is like a puzzle comprising hundreds of different pieces that need to be individually identified and analyzed. Here are five practical tips to help.
1. Securely Deploy and Set up Devices
Typically, industrial operations include numerous legacy devices that are increasingly vulnerable because their networks are no longer always air-gapped (no direct connection to the internet). In an ideal world, legacy equipment is upgraded quickly with advanced systems that include embedded security features.
However, budget restraints and the fact that industrial operations do not experience downtime frequently lead to a mixture of old and new equipment operating together. In this scenario, it’s important to have a security-hardened networking device to enable connectivity for legacy devices.
To ensure that the devices use a secure-by-design methodology, you should check that the embedded security functions of your networking devices adhere to security standards, such as those detailed in the IEC 62443 standard. After confirming this, you can set up devices securely. For instance, we recommend disabling any unused ports and services to minimize available entry points for intruders.
2. Divide Networks Into Multiple Segments
Once the network nodes are securely configured, the next step is to segment your networks following a zone and conduit policy.
Dividing the connected networks into segments to enhance network security helps avoid the scenario in which the entire network goes down because of a single network node being compromised.
A secured network architecture design, such as network segmentation, reduces the risk of threats emerging from the IT network. However, it’s also important to choose the right method for dividing industrial networks into segments.
It is not sufficient to protect an OT environment by simply placing an IT firewall in front of the OT network. However, this advice is frequently ignored. An IT firewall does not have the capability to recognize the industrial protocols that allow cyberattacks to take place at the supervisory or process level.
This leaves the system vulnerable to intrusion.
Firewalls that are used in industrial control systems must segment networks into separate network zones to achieve vertical protection. They also should include the deep packet inspection engine function to filter unauthorized packets without affecting performance of operations and providing horizontal protection.
3. Protect Critical Data and Assets
The purpose of OT/IT network convergence is to collect data and transform it into valuable information.
One good option is to use cloud technologies that are both convenient to use and have powerful data analysis capabilities to simplify network convergence.
However, with cloud technologies, remote access poses a significant security concern. Increasingly, machine builders are leveraging cloud platforms to streamline machine maintenance. Before you are able to reap the benefits, make sure remote access to your critical assets is secure by using features such as data encryption and a VPN.
Vendors, system integrators, and even remote service engineers are essential for daily operations, maintenance, and troubleshooting. They also play an important role in your security policies.
Any capital investment is worthless if these people lack cybersecurity awareness and do not know how to leverage these technologies. To avoid this undesirable scenario, you must ensure that everyone involved in industrial processes has the same mindset and attitude toward cybersecurity.
4. Enhance Industrial Cybersecurity Awareness
According to the security awareness pyramid, cybersecurity can be separated into different awareness stages.
Commitment and support from management forms the foundation, which is followed by security programs and policies being implemented during the awareness-building process. Taking security policies as an example, it is fundamental to define who has Read and Write access based on the security configurations.
However, when these policies are rolled out across an entire organization, it becomes a challenge to ensure everyone adheres to them properly. Facility managers often find implementing cybersecurity measures very cumbersome, and subsequently they do not ensure everyone follows the guidelines. Sometimes they may end up doing things more akin to group-level security, instead of ensuring each individual has their own unique log-in credentials, which subsequently opens up new cybersecurity risks.
Once awareness has been established and policies have been defined, employees will pay more attention to their system settings.
It can be a complex task to examine all the systems at one time, but it is never too late to get started. Performing a risk assessment will help define security priorities. From this position it is easier to identify and protect critical assets. A good starting point is to examine configurations. If a large-scale network is being examined, it is recommended to leverage visualization software to check the security settings and adjust the configurations where necessary.
Alvis Chen is global marketing, integrated marketing project manager for Moxa, 601 Valencia Ave., Suite 100, Brea, Calif. 92823, 714-528-6777, www.moxa.com.
About the Author

subscribe now


Keep up to date with the latest news, events, and technology for all things metal from our pair of monthly magazines written specifically for Canadian manufacturers!
Start Your Free Subscription- Trending Articles
Sustainability Analyzer Tool helps users measure and reduce carbon footprint
Mitutoyo updates its end-user portal
Enhance surface finish with high-speed machining

Equispheres secures $20 million investment round

Solid carbide drills produce precision holes in short chipping materials

- Industry Events
Automate 2024
- May 6 - 9, 2024
- Chicago, IL
ANCA Open House
- May 7 - 8, 2024
- Wixom, MI
17th annual Joint Open House
- May 8 - 9, 2024
- Oakville and Mississauga, ON Canada
MME Saskatoon
- May 28, 2024
- Saskatoon, SK Canada
CME's Health & Safety Symposium for Manufacturers
- May 29, 2024
- Mississauga, ON Canada















